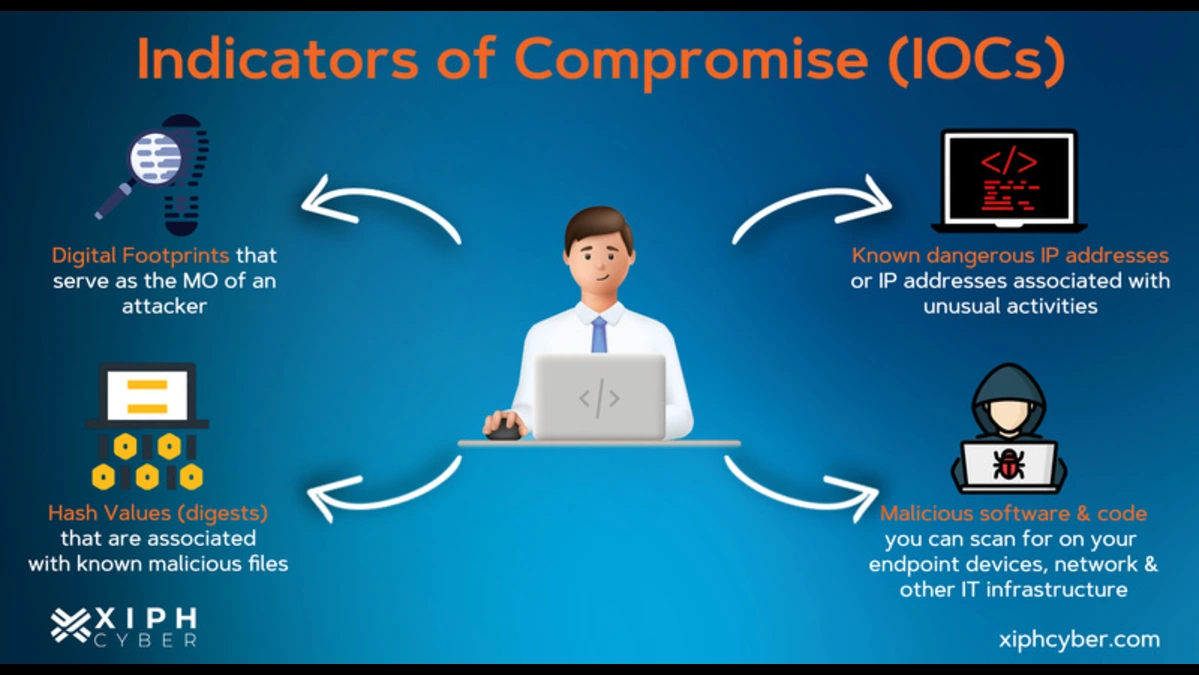
Tag: IOC in Cyber Security: Identifying Indicators of Compromise
IOC in Cyber Security: Identifying Indicators of Compromise
The threat landscape constantly evolves, making cybersecurity a critical concern for individuals and organisations. One…
By
Khizar Seo
Stay Connected
Categories
Must Read
Create an Amazing Tech News Website
Discover thousands of options, easy to customize layouts, one-click to import demo and much more.
Learn More